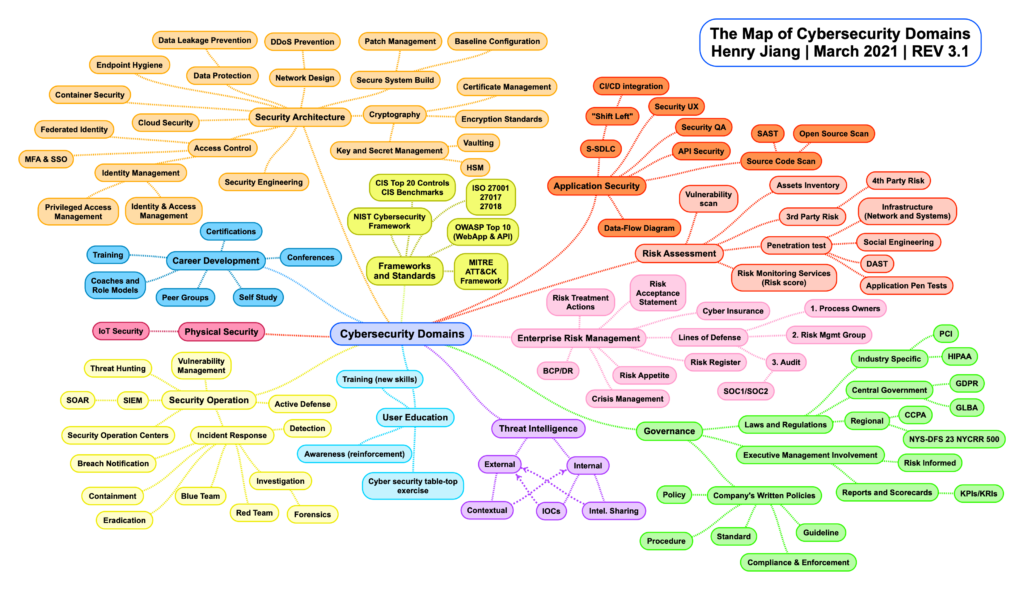
CYBERSECURITY DOMAINS
The Map of Cybersecurity Domains by Henry Jiang | March 2021
The Map of Cybersecurity Domains by Henry Jiang | March 2021
NIST Cybersecurity Framework
CIS Top 20 Controls CIS Benchmarks
ISO 27001 27017 27018
OWASP Top 10
MITRE ATT&CK
- > Security Engineering
- > Access Control
- – Identity Management
- — Privileged Access Management
- — Identity & Access Management
- – MFA & SSO
- – Federated Identity
- – Identity Management
- > Cloud Security
- > Data Protection
- – Data Leakage Prevention
- > Network Design
- – DDoS Prevention
- > Secure System Build
- – Patch Management
- – Baseline Configuration
- > Cryptography
- – Certificate Management
- – Encryption Standards
- – Key and Secret Management
- — Vaulting
- — HSM
- > S-SDLC
- – Shift Left
- – CI/CD integration
- > Security UX
- > Security QA
- > API Security
- > Source Code Scan
- – SAS T
- – Open Source Scan
- > Vulnerability scan
- > Assets Inventory
- > 3rd Party Risk
- – 4th Party Risk
- > Penetration test
- – Infrastructure
- – Social Engineering
- – DAST
- – Application Pen Tests
- > Risk Monitoring Services Scan
- > Risk Treatment Action
- > Risk Acceptance
- > Cyber Insurance
- > Lines of Defense
- – Process Owners
- – Risk Mgmt Group
- – Audit
- – SOC1/SOC2
- > Risk Monitoring Services Scan
- > Laws and Regulations
- – Industry Specific
- — PCI
- — HIPAA
- -Government
- – Regional
- – Industry Specific
- > Executive Management Involvement
- – Risk Informed
- – Reports and Scorecards
- — KPIs/KRIs
- > Company’s Written Policies
- – Policy
- – Procedure
- – Standard
- – Compliance & Enforcement
- – Guideline
- > External
- – Contextual
- – IOCs
- > Internal
- – Intel Sharing
- – IOCs
- > Training (new skills)
- > Awareness (reinforcement)
- > Cyber security table-top exercise
- > Vulnerability Management
- > Threat Hunting
- > SIEM
- – SOAR
- > Active Defense
- > Incident Response
- – Breach Notification
- – Containment
- – Eradication
- – Blue Team
- – Red Team
- – Investigations / Forensics
- > Security Operations Center
- > IOT Security
- > Certifications
- > Conferences
- > Self Study
- > Peer Groups
- > Coaches and Role Models
- > Training
Security through data
Emerging Technologies
Frameworks
Repository
© 2023 | CyberMaterial | All rights reserved.
World’s #1 Cybersecurity Repository


